7-1 Project Overview
With the development of Internet technology, network security threats to critical infrastructure have increased year by year. Based on the critical infrastructure security obligations, Taipower has cooperated with the government’s top management to actively promote the national policy of “Cyber Security, National Security” and the “Fifth National Security Development Program (106-109) of the Executive Yuan”. The Information Sharing and Analysis Center (ISAC) is built in tandem with the E-ISAC platform currently being built by the Ministry of Economic Affairs (MOEA). To build a security mechanism for emerging information technology, Taipower enhances the security management and continuous operation of critical infrastructure by strengthening the security protection of critical infrastructure through the analysis and sharing of security information.
7-1-1 Build Range
The system is built in the Taipower intranet, and any Taipower employees can apply for the TPC-ISAC platform member account to share the information. TPC-ISAC system is connected to the ISAC of Ministry of Economic Affairs (E-ISAC) as shown in Figure15.
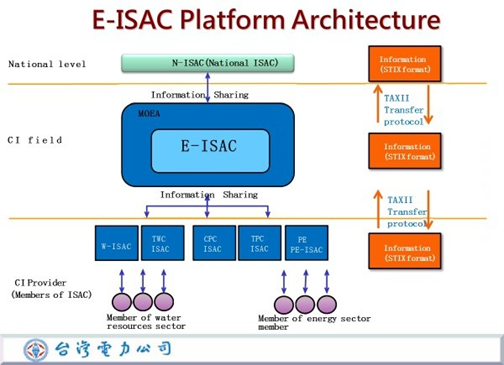
Figure 15 E-ISAC platform architecture
7-1-2 System Functions
Alert Release
The user of this operation accesses the web server of the system through the web browser of the Taipower enterprise website (Single Sign-On system) through a WEB browser and reads the relevant public information stored in the database of the system.
The Security Information
SharingThe member account permission module of this operation includes the system account management and can set its associated account group and authority. Besides, when the user account is logged into the system through the account rights management module, user appropriate permissions is shown as Figure 16.
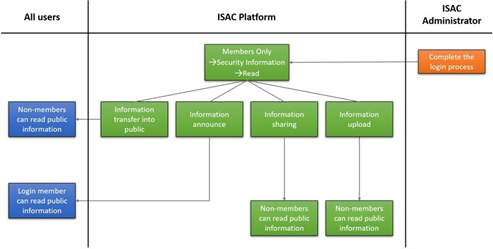
Figure 16 Information management process
Public Information
Users use the browser to access the web server system by the Single Sign-On system of the Taipower enterprise website and read the relevant public information stored in the database of the system.
Data Enquiries and Statistics
Managers can use the “Classification Enquiry” function to query specific/unspecified fields for security information or incident notifications, such as specific period inquiries, specific field content, and specific classification queries, etc. The information is to comply with N-ISAC affair and event categories. Follow the N-ISAC definition of interest to ensure that the exchange of benefits is healthy.
Unified Information Format
Through the system automation and standardized format for information sharing, and refer to the N-ISAC information exchange specification of the Executive Yuan, conduct related information exchanges with the relevant domestic E-ISAC (such as the Ministry of Economic Affairs) to provide information on the incidents of the security incidents, web threat information and contingency measures.
STIX (Structured Threat Information eXpression) Information Format - — CybOX (Cyber Observable eXpression) Standard word
TAXII (Trusted Automated eXchange of Indicator Information)
The information content is described and packaged using CybOX and STIX, and data are exchanged through TAXII. Refer to Figure 17.
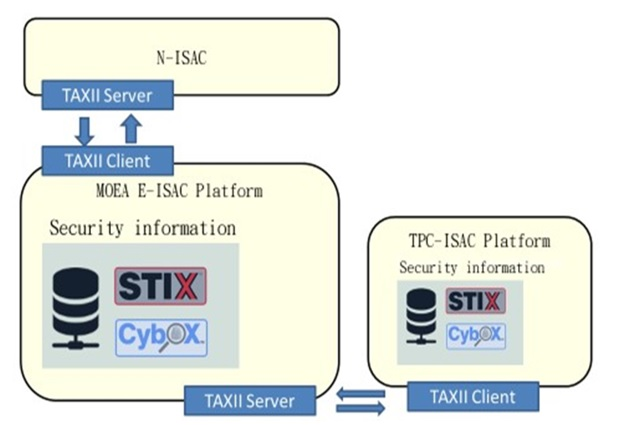
Figure 17 ISAC information format
All systems of this platform run on the virtual server in the Taipower intranet, and are connected to the E-ISAC platform currently being built by the Ministry of Economic Affairs. The system uses a three-tier architecture design, which is a general application of web server, web application, and database. At thesame time, to access the TPC-ISAC platform through a personal computer or mobile device, the front-end display mechanism of the platform uses Responsive Web Design (RWD), which automatically determines the type of device used by the user and select the appropriate display. The working environment is planned as shown in Figure 18.
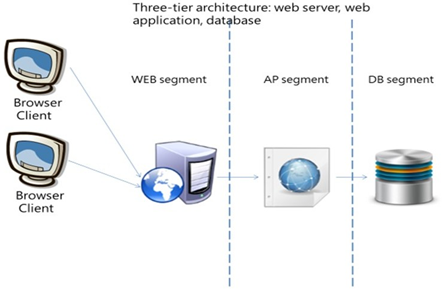
Figure 18 ISAC three tiers architecture
7-2 Security Requirement
The Taipower TPC-ISAC service platform has the following security considerations:
7-2-1 Comply with the “Safety Software Development Life Cycle” Specification
According to the development needs, we write various standard development documents and conduct system threat analysis in the system design stage, and design appropriate security measures based on the analysis results to improve system security. This platform is based on the SSDLC process and focuses on the security requirements of the information system. It includes “Confidentiality”, “Integrity”, “Availability”, “Authentication”, “Authorization and Access Control”, and “Log” depending on the type of software. It records “Talk Management”, “Error and Exception Handling”, “Configuration Management”, etc., to check the security level of the system platform.
7-2-2 Platform System Vulnerability Scanning
Before the platform is launched, the vulnerability scanning and source code detection are performed to ensure that the delivered application system has no backdoor or Trojan horse programs, and all the issues are addressed before going online. Regarding source code detection, this platform uses the white box source detection tool to provide two security tests at the beginning stage and after the repair, and cooperates with professional security consultants to analyze the source code test results, and provides suggestions for improvement on the discovered security breaches. Program developers understand system application vulnerabilities and analyze their risk severity based on vulnerability scan reports, which can effectively reduce the barriers and cognitive gaps in system application patching and improve the effectiveness of vulnerability patching.
7-2-3 The User Establishes an Audit Authorization System
When logging in to the platform, the high-privilege account needs to input a graphic verification code (CAPTCHA) and a one-time verification password (OTP) sent by the platform to the mobile phone as a second login credential other than the password. After the user logs in successfully, the default is the minimum privilege. If you need to obtain a higher privilege, you need to be authorized by the system administrator. The TPC-ISAC authorization system is shown in Figure 19.
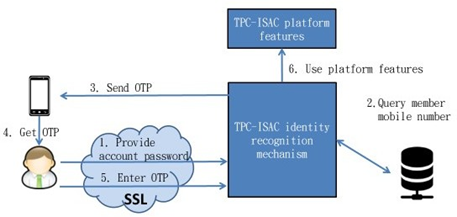
Figure 19 TPC-ISAC authorization system
7-2-4 Data Backup
The platform automatically backs up the database file and application configuration files every day and conducts disaster recovery exercises to ensure that the backup mechanism works perfectly.
7-3 Cyber Threat Warning Mechanism
Threat lights are based on a variety of objective environmental factors, after a process evaluation and calculation procedures, showing the quantitative risk indicators of potential threats to the underlying system. The primary purpose of the threat signal is to reflect the overall risk profile of the system security, with a simple and easy-to-understand indicator to show the degree of risk at a glance and to take action. The platform’s OT and IT threat rating is based on the US Department of Homeland Security’s threats to physical security, terrorist attacks, and security threats. These threat lights are based on the threat level of terrorist activities or criminal activities, and set five threat levels, including green light (low alert), blue light (start alert), yellow light (alarm alert), orange light (high alert), and red light (severe alert).
Referring to the definition of the lights as mentioned earlier, when the platform encounters a security situation, it first needs to determine the scope and object of the threat, and secondly, it needs to determine the source, scale, certainty, and level of the threat. Consider IT-related information security threat warnings, malware statistics, vulnerability database, OT entity security, personnel security, security incidents based on various objective environmental factors. After specific evaluation and calculation procedures, the IT and OT targeted systems are subject to potential threats, quantified risk indicators, showing the overall risk and threat status of system information/network security. The establishment of image-based security threat lights, making it easy for viewers to use easy-to-understand indicators. Determine the degree of risk and take appropriate action accordingly. The illustration of threat light is shown in Figure 20.
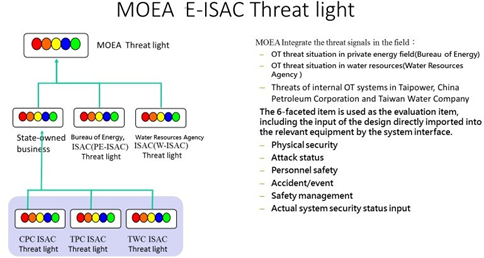
Figure 20 ISAC threat light
In order to effectively achieve the sharing of security information, the Taipower TPC-ISAC platform needs to communicate effectively with other critical infrastructure members and the competent authority ISAC, such as regular meetings or questionnaires to obtain feedback to improve the sharing mechanism continuously.
In the past years, the Executive Yuan has vigorously promoted the provision of critical infrastructure units to build their ISAC platform, consider non-technical aspects of security protection, adopt information sharing methods, and automatically share security threats and messages in various fields to achieve rapid integration of information. The purpose of sharing and practical application is to enhance the overall response and protection capabilities of security information and achieve the goal of cybersecurity.