5-1 Commitment to Maintain Customer Data Security
Taipower was committed to providing comprehensive power delivery and selling service for customers therefore ted a lot of related information. In order to protect customers’ data, apart from Taipower information security management system, Taipower also obeys privacy policy, security policy, and related laws.
Taipower has established policies, controls, and procedures in place to protect every customer’s personal identifiable information and applicable energy usage data. For maintaining customer data security, high-level data protection and privacy strategy cover the data protection strategies for Smart Grid as more new types of data, such as 15-minute usage through the meter and billing information summary is generated and made available to customers.
Based on Taipower information security management system(ISMS) and Taiwan government’s information security requirement, six levels of perspectives ranging from business process, application system, database management system, operating system, network environment, and physical environment, are needed to strengthen in the area of information security strategy, policies, management, deployment, monitoring, and system development, in order to meet the standard of protecting customer data and privacy.
Moreover, based on Taipower regulation, all customer data are required to be classified into groups for all application system, in order to distinguish the life cycle of data information which is of the nature of agility. According to the requirement of data access security management procedure, different roles of duty and importance should be assigned in regard to user’s different access rights, in order to design an effective security access control principle for agility information. Throughout a top-down design application system will need to strengthen the ability in information security access control from the get-go, subject matter such as application system role authentication, system function access right design, agile data usage track record, and other non-business oriented task are essential for security requirement and should all be included in evaluation category.
5-1-1 Collection and Application of Customer Data
Personal information that Taipower collects:
- Names
- Street addresses
- Telephone numbers
- Email addresses
- Account numbers (including utility account numbers, credit card numbers, bank account numbers)
- Meter identifier and meter interval/electricity use data that are released in combination with any information included in items above
- Taipower uses personal information to:
- Establish and provide ongoing service
- Communicate with customers
- Verify identity and protect against error or fraud
- Manage invoicing and customer services
- Monitor customer satisfaction with our programs and services
- Provide aggregate information for government agencies & open data - – - Comply with legal and regulatory requirements
- Tailor recommendations that help customers save energy
- Administer our websites
- Gather management information to form statistical and trend analysis
- Open data
5-1-2 The Policy of Security that Taipower Obeys
1. Taipower ISMS Policy
Purpose
Using information technology actively to strengthen the operational management of the company and let the company can grow and operate in a stable and secure environment. Therefore Taipower should establish a comprehensive ISMS mechanism to implement the idea that “ISMS is Everyone’s Responsibility”. Therefore this specific policy is set to ensure the integrity, confidentiality, availability, and legality of critical information assets and information infrastructure.Principle
- Information assets and key information infrastructures should be regularly enumerated, classified and graded. Risk assessment should be conducted for important information assets and key information infrastructure, and appropriate protective measures should be implemented accordingly.
- The act of collecting, processing and using customer data should conform to the “Personal Data Protection Act”.
Unit leaders should pay attention to confidentiality, identification, and control of sensitive information, for funding through security policies, regulations and norms of the work to follow should bear responsibility monitoring, enforcement and auditing of, and the exact implementation of routine operations in all units and staff in daily work. - A complete notification and contingency measures are required for the ISMS incidents, and regular security exercises are held to ensure the continued operation of the business.
- All employees should fully understand the purpose and responsibilities of the ISMS policy. Regularly review the effectiveness of the safety management system.
- This policy and related operating practices should be appropriately revised based on business changes, information technology development, and risk assessment results.
Scope of application
All employees who use the company’s information assets, key information infrastructure and supplemental workers should comply with this policy.
Implementation
In accordance with the “ISMS Implementation”, “ISMS Operational Manual”, “ISMS Safety Teaching Manual”, “ISMS Internal Auditing Operation Key Points “, “ ISMS Emergency Response Plan and Operation Processing”, “Personal Data Protection Management Key Points”, and”Personal Data File Security Maintenance Plan and Personal Data Processing Method after Business Termination”, Taipower ISMS Policy is implemented.
2. Privacy policy
- The website collects personal data from users and complies with the laws of Taiwan on the Protection of Personal Data. Without user consent, the user’s personal data will not be collected by the website.
- The website automatically records the pages requested by the users and collects addresses from visitors, and uses the information as the basis of system improvement, and evaluation of policy announcements. That information is only used for statistical analysis of data and does not involve personal data of users.
- When the user browses the website of Taipower, the website will place a cookie (a small descriptive text file) on a user’s personal computer or smart device. This cookie does not contain enough information to identify the user’s personal identity. Instead, it records the personal services and other information that the user sets on this page. The Taipower website server can only read the activity record of the user’s cookie on the website, and cannot read the user’s activity record on other websites.
- This privacy protection statement will take effect from now on. However, in response to changes in the social environment and laws and regulations, and the advancement of science and technology, the Taipower has the right to modify this statement and update and announce it as soon as possible.
3. Security policy
- Network Security Measure
To protect this website and to ensure that this service is provided to all internet users, this website has taken the following security measures:
- Utilization of the network intrusion detection system to monitor the network traffic and capture any unauthorized attempt to upload, change or destroy website content.
- Employing firewalls to prevent any unauthorized intrusion, destruction or theft of the information in order to protect the website from any illegal access and to protect the website users’ rights.
- Installation of anti-virus software. The system is scanned for virus periodically to provide a safe web browsing environment.
- Drills of hacking attacks to the website are held on an indefinite schedule to test the system recovery process in times of a real security breach and to provide a proper protection level.
- Daily data backup makes a copy of all the data to the redundant server every day.
- Acts in accordance with the suggestions provided by any notice from the system and software developers and takes proper action such as the installation of the latest security patches.
User Privacy Protection Measures
Customers should be taught to keep their password or any personal information from anyone else’s access.Do not provide any personal information, especially their password, to anyone else. After users finish online registration, email reading or any administrative functions, they have to remember to log out. If they are sharing a computer with anyone else or using a public computer, they have to remember to shut down the browser after they complete their tasks to prevent any other users of the computer to access their personal information, email or entering the administrative area of the website.Revision of the Security Policy
To fulfill our objective of providing our customers the best network security, Taipower will improve the security measures on our website to adapt to the technological advancement, revision of relative regulations and unforeseeable environmental changes. Any change to our security measures will be announced on our website immediately with bold headlines to capture customers’ attention.
Security Measures Q&A
If our customers have any questions concerning our network security measures, Taipower have a website for them to contact us at any time.
5-2 Data Protection Best Practiced in Taipower
5-2-1 Firewall
Employ a firewall to keep criminals out and sensitive data in.
With the latest security software, web browser and operating system are the best defenses against viruses, malware, and other online threats. Following our policy automatically connect and update to defend against known risks for software programs.
5-2-2 Implementing a Robust ISMS Awareness Program for Employees
Employees are often the handlers of customer data. They, therefore, need to be kept up-to-date on how to protect that information to make sure it does not accidentally land in the wrong hands. Our employees are periodically educated about the newest security attack and defense schemes and urged to employ best practices such as not responding to or opening attachments or clicking suspicious links in unsolicited email messages.
5-2-3 White-box Testing
Web applications are our center of business innovation and provide services for our customers, but they are also the primary attack vector for malicious individuals seeking to reach your organization’s defenses. For application security must be a priority, we use white-box testing technology to find common and potential vulnerability like an SQL injection in applications.
5-2-4 Database Activity Monitoring
We follow reasonable security measures to ensure that customers’ and employees’ personal information is protected from inappropriate and unauthorized access. Identifying and reporting a database’s activities by database activity monitoring tools, we use real-time security technology to monitor and analyze configured activities independently and without relying on the DBMS auditing or logs.
While the wide range of useful information is accessible through the web, outside access to data is controlled through authentication, authorization, and audit mechanisms, such as dbAegis(Database Activity Monitoring)(Figure 6).
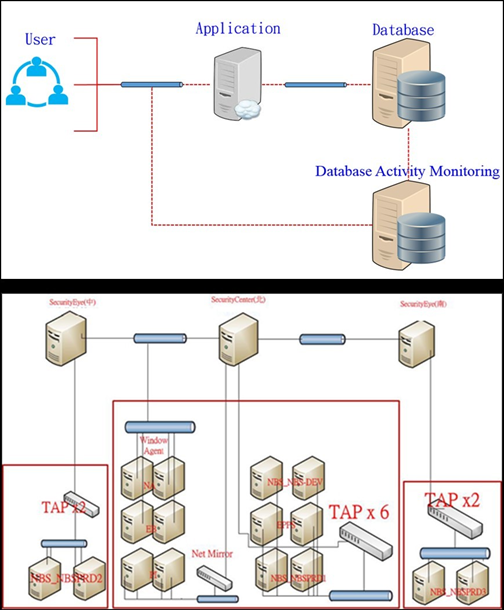
Figure 6 Database activity monitoring architecture in Taipower
5-2-5 Transmittal of Data
Taipower uses SSL (Secure Sockets Layer) as the encryption algorithm. SSL at the transport layer encrypts the HTTP traffic coming from the application layer. It adopts public-key cryptography to keep an internet connection secure and reliable,safeguarding any sensitive data that is being sent between customer and server, and preventing criminals from reading and modifying any information transferred, including potential personal details. Current websites and browsers generally combine HTTP with SSL to attain safe communication.
When a user is accessing data, the SSL encryption packet will be used to transfer data. Even if the packet is intercepted by people with bad intention, they still cannot decrypt it or read it.
5-2-6 Authentication
On authentication, with the account lockout mechanism, after a user’s account fails to login to verify the identity for 3 times, the account and the source IP are not allowed to continue trying to login for at least 30 minutes. Besides, when the password is concatenated by a random number (Salt) and processed with a hash function, the random number and the resulting output (but not the original password) are stored separately to safeguard passwords in storage. We also use the CAPTCHA mechanism for authentication and important transaction behavior to prevent attempts by automated programs. When users need to reset their password, or the system has to interface with an external system, they will be asked for re- identification, and afterward, we will send them a one-time and timeliness token. After receiving and checking the returned token, they are allowed to reset their password or connect to the external system.
5-2-7 Encryption for the confidential data
In the foreseeable future database columns which consist of confidential information such as personal identification number, bank account, and user address will all be encrypted. Encryption poses little to no effect on system performance, thus essentially transparent. After encryption even if the data is fetched from the physical database, without the correct decryption the data will remain unreadable, thus incomprehensible. As for users who are given the legal access rights, decryption will be executed in the background automatically.
5-2-8 RACF
The mainframe uses a resource access control facility (RACF) to protect resources by granting access only to authorized users of the protected resources. RACF retains information about users, resources, and access authorities in special structures called profiles in its database, and it refers to these profiles when deciding which users should be permitted access to protected system resources.
To accomplish access control, RACF provides the ability to:
- Identify and authenticate users
- Authorize users to access protected resources
- Log and report various attempts of unauthorized access to protected
- resources Control the means of access to resources
- Allow applications to use the RACF macros
5-2-9 Sensitive Information and Privacy Data Protection Policy with AMI System
Table 2 security policy with AMI syatem
5-3 Policies & Compliance
For the sake of enabling the corporation to operate efficiently and grow in a secure and stable environment, we follow our company’s ISMS policies, actively applying information technology, strengthening operational management, and implementing the concept of “Cyber Security is Everyone’s Responsibility”, thereby attaining the confidentiality, integrity, availability, and legality of the information assets and critical infrastructures.
Annually, our ISMS execution group convenes the meeting to determine the priority of the risk management information assets and acceptable risk values based on the results of the risk assessment. It follows the “Asset Categories and Weaknesses, Threat Correspondence Table”, “Weakness Vulnerability Score Table”, and “Threat Probability Table” to identify the actual risks and measure the existing controls of information assets. The group formulates a risk management plan to check whether the existing controls are sufficient for reducing the risk to an acceptable level. If not enough, safety control measures must be added. After the proposed new control measures are formulated, the person in charge and the due date of the improvement plan should be assigned according to the “Procedures for the Safety Precautions Management Procedure”.After the improvement is completed, the residual risk is assessed and the above content is filled in the risk management plan. Taipower also has complete notifications and contingency measures for the security incidents, and holds security exercises regularly to ensure the continued operation of the business.
A good control describes the organization’s approach to managing information security and its implementation (i.e. control objectives, controls, policies, processes and procedures for information security) is reviewed independently at planned intervals or when significant changes occur. In addition to holding an internal audit of important information assets and critical infrastructure security at least once a year, annually Taipower also gets an independent review of security risks and controls through external agencies like BSI to ensure impartiality and objectivity as well as benefit from fresh eyes, and benefit from another colleague reviewing policies besides the main author/administrator. These reviews are carried out at planned, regular intervals and when any significant, security-relevant changes occur – ISO compliance reviews regularly to be at least annually.
The collecting, processing and utilizing personal information shall comply with the provisions of the Personal Information Protection Act. Taipower only shares customer information with the public in compliance with the Personal Information Protection Act. As a public utility, Taipower will seek to protect the privacy of our customers’ personal information in complying with public records requests. Penalties for violations of the Personal Information Protection Act may be a fine of NT$20,000 to NT$500,000.
In order to lessen the likelihood of a cyber attack, Taipower puts the right people and processes in the right place.
Taipower also coordinates with government agencies and stakeholders to best protect our energy grid and technology systems, share information and develop protective standards. Working with industry partners and vendors, the company ensures it’s taking steps to protect systems and data.
Taipower has detailed cybersecurity reporting requirements and strong partnerships to prevent and respond to threats. Our company’s businesses have mandatory and enforceable cybersecurity standards to protect critical infrastructure. These extensive measures help keep networks safe and prevent those wanting to do harm.
New security policies will be developed, and existing policies modified, to address emerging personal privacy issues. Privacy protection measures are designed into Smart Grid solutions and standards as part of the solutions delivery cycle. Taipower will continue to develop and deploy personal privacy training and awareness programs, and also will introduce new data protection measures such as data encryption tools.Taipower implements the “Information Security and Personal Data Protection about Outsourcing Service Providers Audit Plan” each year, which is involving the Legal Affairs Office and the Department of Civil Service Ethics. In addition, the higher authorities, the Bureau of Energy, of the Ministry of Economic Affairs, will also form a special audit team to check the personal data protection situation of each unit of the Taipower Company each year.